Over the past few years, Internet technologies have deeply penetrated human everyday life. Today, banking, trade, services and entertainment operate successfully online. But with such technological breakthroughs, online fraud is also flourishing everywhere. As usual, the main goal of scammers is to lure money out of the user and disappear into the vastness of the Internet. In this article we will describe the main directions in which online scammers operate, and we will also tell you where to go to get your money back first.
Let's start with a description of the most common areas in which scammers operate. We will be based on our own experience.
Fraudulent online stores
This is the most common deception scheme that gullible users fall into. Today it costs nothing to create a fake online store and launch “trade” of non-existent goods on it. Advertising is ordered online, positive reviews are generated, and prices are quoted extremely low. All these subtleties lull the vigilance of users who send money to scammers without basic checks. Payments are accepted online and by cash on delivery, but all this happens before the fraud is discovered. With all this, the creator of such a marketplace remains in the shadows and is able to easily erase traces of his activities by simply deleting the site and blocking the “official” number of the store.
Fraud in online stores can be as simple as a seller accepting money and disappearing, or quite complex, where a whole scheme is created to sell substitute goods. Such a scheme involves official organizations and third-party recipients of money, so it becomes very difficult to prove the fact of deception. We have already written about such schemes several times; we recommend reading the article about PIM-MAIL LLC and the LLC Parcels Pro online store.
Deception through ad sites
In the case of advertisements, scammers work in two directions - they deceive both sellers and buyers. The standard scheme prevails: a person sees an ad, orders a product and makes an advance payment, but in the end nothing comes to him and the seller disappears. There are quite a lot of scam schemes with advertisements, and on the most popular resource Avito, scammers successfully bypass the special “Safe Transaction” function. Here are some examples:
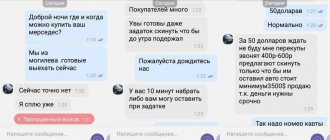
- They write to the seller directly via (Whatsapp, Viber) and offer to purchase his product. Referring to a secure transaction, a fake electronic receipt indicating prepayment is sent to the seller’s email. After some time, the scammer writes that he has changed his mind and asks to send the advance payment back - people are fooled.
- They communicate with the buyer through messages on Avito, but “for convenience” they switch to a third-party messenger. Next, the buyer is sent a link to a fake website where he can make an advance payment (under the terms of the “Safe Transaction”). Very often people do not notice the substitution and transfer money.
An attempt by scammers to provide a link to a fake website
Making money through subscriptions
Also very popular on the Internet is the scheme of issuing paid online subscriptions to second-rate services. Such services include dating sites, loan selectors, and online cinemas. The deception process involves hacking a bank card and linking it to purchase online services. A person simply discovers that a debit has been made in favor of a fictitious dating site. After contacting support, the person is shown a personally signed subscription.
This is the most difficult process for a defrauded cardholder, since it is very difficult to prove the intervention of third parties. It’s easy to guess that the owners of the service personally activate people’s hacked cards, but it’s impossible to prove this fact. As a result, hackers legally withdraw money from hacked cards.
To understand the danger and scope of such fraud, we recommend reading our articles about the dating site LoveDateme and the loan selector Qzaem.
“Legitimate” withdrawal of funds in favor of a Banando subscription
Deception through spam mailings
We will call the simplest and slightly naive type of fraud spam mailings that report a “million dollar win” or “inheritance under a will.” Such notifications must include a link to the scammers’ website, where you need to pay a certain amount to process the payment. Most often these are fake lotteries, fake notifications from the tax office, notifications about government payments. This type of spam is distributed via email, SMS, Viber or WhatsApp. Oddly enough, people fall for such alerts and transfer money by flashing their bank cards.
Spam from loan selection sites
Methods of fraud in online stores
The popularity of electronic trading platforms attracts scammers to this niche. There are many methods of deception. The most commonly used are:
- The buyer made an advance payment or paid for the goods in full, but never received the order. In these cases, they are most often asked to make a transfer to an individual’s card. At the same time, the person with whom the buyer communicates and the person indicated by the recipient of the funds may not coincide.
- The sent product turned out to be unusable - broken, damaged, expired, and so on. In this case, the seller does not get in touch, or simply refuses to compensate for the damage, citing the fact that he sent a normal item, and the buyer himself damaged it.
- The product sent does not meet the stated specifications.
- The cost of the product turns out to be more than originally agreed.
You can avoid deception: pay for the goods only upon receipt, after inspection, checking functionality, expiration date, and compliance with the declared technical characteristics.
Note!
If you are not satisfied with the product, then according to the Law “On the Protection of Consumer Rights” you can return it within 14 days and get your money back.
Preventive measures
Mandatory
| Action | Explanation | |
| 1 | Set a PIN code on the SIM card | in case of loss/theft of your smartphone, the swindler will not be able to quickly use your number, you will gain time |
| 2 | Apply at the mobile operator’s office for a ban on actions with a power of attorney | to prevent crooks from making a duplicate SIM card using a fake power of attorney |
| 3 | Issue a ban on registering real estate transactions without personal presence | to exclude the sale of an apartment using a fake power of attorney or fake digital signature |
| 4 | Set up a notification about the issuance of an electronic signature in your personal government services account | if fraudsters issue a fake digital signature in your name, you will know about it immediately |
| 5 | Set up two-factor authentication on government services, tax, mos.ru, and Rosreestr websites | scammers will not be able to log in even if they find out the password |
| 6 | Install caller ID on your smartphone | in most cases, scammers call from numbers marked as fraudulent. But sometimes they replace the number with a real bank number, then see point 40 |
| 7 | Install antivirus on your smartphone | protection against Trojans, stealers and other malware |
| 8 | Keep your smartphone software updated regularly, including security updates | protection against current attack methods and closing vulnerabilities |
| 9 | Create different passwords for different sites and applications or use a password manager | if the password for government services matches the password for a simple forum, then by hacking this forum a hacker will receive a password for government services |
| 10 | Set up an alert for each login to the government services website | if scammers gain access to your account, you will know about it immediately |
| 11 | Set daily spending and transfer limits on a bank card | Fraudsters will not be able to withdraw more than this amount. It will be difficult to increase the limit |
| 12 | Configure receiving confirmations of banking transactions via push rather than via SMS | SMS is an unreliable protocol and is susceptible to eavesdropping and attacks. However, if you are leaving for an area without Internet or in roaming, temporarily return the SMS notification |
| 13 | Apply for a ban on the “Mobile transfer” service at the mobile operator’s office | if the SIM card is compromised, money will not be withdrawn from it |
| 14 | Set your smartphone to hide notification texts on the lock screen | If your phone is stolen, scammers will not be able to read bank codes on the locked screen |
| 15 | Set a code word in the office of your mobile operator | for quickly blocking a SIM card in emergency situations |
Important
| 16 | In your Google (Apple) account, indicate a spare phone number and a spare email | if your account is compromised, this will be needed to restore access |
| 17 | Set your smartphone screen to auto-lock for no more than 30 seconds | if the phone is stolen, it will have time to be locked |
| 18 | Remember the code words and security questions for all the banks you use. | so that in emergency situations, without wasting time, confirm your identity in the call center |
| 19 | Don't choose security questions that are easy to answer, such as your mother's maiden name. | this information is often publicly available or in purchasing databases |
| 20 | Learn by heart the numbers of your loved ones | to call loved ones from a number other than your own in emergency situations |
| 21 | Connect alerts about your credit history inquiries | you will be immediately notified of any intention to issue a loan to you |
| 21.1 | Connect notifications about card transactions | this will allow you to quickly identify fraudulent charges and call the bank without wasting time |
| 22 | Keep the phone number linked to your bank account with you at all times. | If a fraudster issues a duplicate SIM card, you will immediately know about it. Why you can’t keep a separate SIM card for banking transactions |
| 22.1 | For the main card you use to pay in stores and on the Internet, prohibit cash withdrawals and purchases outside your country | Stolen cards are usually used in other countries. If you need to pay for foreign goods/services, create a separate virtual card for this. If you go on a trip, temporarily lift this ban |
| 22.2 | When paying online, do not enter your card details in a pop-up window where the payment system website address is not visible | scammers can create a complete copy of the payment page, but it will lead to a fraudulent server |
| 23 | Disable auto-save passwords on your smartphone and computer | otherwise, if the phone is stolen, the thief will be able to see all the saved passwords, incl. those that were saved from the computer |
| 24 | Set limits on auto-replenishment of SIM card balance | If the SIM card is compromised, scammers will not withdraw all the money from the bank card |
| 25 | Write down the hotline numbers of banks and mobile operators on your main and backup phones | so that in emergency situations you can quickly find and call the hotline |
| 26 | Disable auto-receive MMS on your device | there is an old vulnerability that allows viruses to be downloaded to the device via MMS |
| 27 | Deprive the rights to view SMS and calls from those applications that do not need it | a Trojan can be embedded in a harmless application that has rights to SMS |
| 27.1 | Check the extensions in your browser, remove unused extensions | scammers buy old extensions and upload malicious code as updates |
| 27.2 | Review the applications on your smartphone, remove unused and old ones | scammers buy old applications and upload malicious code as updates |
| 28 | Set up push notifications for emails | so as not to miss an important notification from a government or banking service |
| 29 | Mark as not spam the phone numbers of the mobile operator and banks you use | so as not to miss SMS regarding security |
| 30 | Install antivirus on your home computer | Protects against viruses, Trojans, spyware |
| 31 | Keep your home computer up to date with the latest operating system and application updates, including security updates | this will allow you to close detected vulnerabilities, protect yourself from attacks and the latest versions of viruses |
| 32 | Disable the ability to connect remotely to your computer: disable remote desktop, close external ports | One of the common hacking methods is to try to brute force open ports from potential victims and use simple passwords for Remote Desktop. |
| 33 | Service at the bank through a call center where you cannot change the linked phone number | scammers obtain personal data in different ways and can link their phone to the victim’s account |
| 34 | Set a fingerprint or password for contactless payment with your smartphone (or disable it) | if a cell phone is stolen, the thieves will not be able to pay them |
| 34.1 | On your Wi-Fi router, set a complex administrator password and change the device’s IP address | so that crooks cannot log in as an administrator on a wi-fi router |
| 34.2 | Set a complex password to connect to your Wi-Fi router | to prevent crooks from brute force guessing the password |
Desirable
| 35 | Carry a spare phone with a working SIM card | to quickly block your main phone if it is lost or stolen |
| 36 | Set a PIN code on your smartphone to view files, photos and open instant messengers | if your phone is stolen, your files, contacts and correspondence will not fall to scammers |
| 37 | If possible, prohibit remote access recovery via remote channels | If you forgot your password, create a new account |
| 38 | Apply to the Federal Tax Service for a ban on registering a legal entity using an electronic digital signature | to exclude registration of an individual entrepreneur or LLC in your name using a fake digital signature |
| 39 | Do not use face unlock on your smartphone | If your phone is stolen, the thief can unlock the smartphone using a photo. The likelihood of this happening is low, but it happens, so it's best to protect yourself |
Where to go if you were deceived in an online store
First of all, you need to contact the portal administration. It is quite possible that the manager simply got something wrong or does his job poorly. In this case, the administration must resolve the conflict and fulfill its obligations to the buyer honestly.
If the online store fails to fulfill its obligations, you need to file a complaint. You can send it to:
- To Rospotrebnadzor.
- To the territorial police department.
- To court.
The latter is best used when appeals to the first two authorities did not give the desired result.
Note!
In case of particularly large-scale fraud, an offer to purchase prohibited goods (weapons, narcotic substances), you can also write a statement to the territorial department of the prosecutor's office.
What to do if the store sent the wrong order
In this case, you can do the following:
- Contact the online store manager and explain the current situation. Before this, you can take photographs of the product and shoot a short video review. It should contain not only the product itself, but also packaging, invoices, and receipts.
- If the manager refuses to correct the error, you can try to contact the owner of the online store directly and solve the problem.
Note!
You need to contact your local police department and file a complaint. The parcel itself will most likely be seized as evidence.
How telephone scammers work
Fraud is gaining momentum due to the huge amount of information about potential victims. Criminals obtain it on illegal markets, where data from online stores, government agencies and financial institutions are leaked.
Moreover, the schemes of fraudsters are gradually becoming more complex. They can spend a long time processing the victim in order to get the desired financial transfer from her. For example, promising unearthly benefits, a high position and attractive payment conditions. They may even arrange a video interview with a potential employer.
How to prove that money was sent to an online store
Note!
It is imperative to save all payment documents that are related to the order: payment receipts, issued invoices, payment details, checks for payment of delivery from the post office.
If the store does not issue an invoice, but simply provides payment details in personal correspondence, be sure to take a screenshot of these messages. The transfer to the card also needs to be recorded - this can be a check from the terminal, from a bank cash desk, or an account statement if you paid via Internet banking.
When paying, be sure to indicate the purpose of the payment - payment for the product and its exact name, including the article number, if any.
What numbers should you not answer calls from?
The activity of telephone scammers in Russia in 2022 is such that a safe option would be not to answer calls from unknown numbers at all (unless the specifics of your work provide for this), since the likelihood that it is a scammer or spam is very high.
Anton Kukanov
Head of the Center for Digital Expertise of Roskachestvo
– If the very fact of answering the call will not cause you any harm (the story about how you supposedly can’t answer with the word “yes” because they will steal your voice sample and then confirm the money transfer is just a horror story), then what you really shouldn’t do is This is to name your bank data - CVC codes and codes from SMS. No bank will ask them.
Where to contact in case of fraud
Fraud is a criminal offense under Article 159 of the Criminal Code of the Russian Federation. But, if the amount of damage is up to 1000 rubles, then the seller’s actions will be considered an administrative offense. In this case, he faces a fine or administrative arrest for up to 15 days.
Under the article “fraud,” the sanctions are more stringent: the fine is up to 120,000 rubles, and correctional or compulsory labor is also imposed. Placement in a penitentiary institution is not excluded.
The statement to the police must include the following information:
- To whom and where should the application be submitted?
- Your personal data as an applicant: full name, passport details, contact details, place of residence.
- Circumstances of the case: when, where and what goods were ordered. Payment method and amount that the victim transferred to the seller, further actions of the seller after payment. Reason for the statement: the goods were not sent, the wrong or damaged goods were sent, what measures were taken to resolve the issue and their consequences.
- List of attached documents.
- Date and signature.
○ What is indicated in an application to law enforcement agencies?
The application is drawn up in free form indicating:
- Details of the recipient and applicant.
- The essence of the appeal (description of the situation of loss of property).
- Indication of legislative norms (Article 159 of the Criminal Code of the Russian Federation).
- Clarification that they are familiar with the punishment for giving knowingly false testimony.
- List of applications.
- Date, signature.
The application should be accompanied by all available evidence of the unlawful act (payment checks, transfer receipts, etc.)