For several months I studied the topic of Internet fraud in order to collect the most complete list of actions that would protect me from scammers and their machinations. The result of the study was a checklist that I want to share with everyone. Its goal is to make hacking digital assets difficult and pointless.
I suggest the reader complete as many points as possible on this checklist, but I must say that this will involve some inconvenience when using a smartphone. But here everyone chooses: convenience or safety. You quickly get used to the inconveniences and they cease to be such, and as for security, hacking any of your accounts can cost a lot of money, time and nerves.
For convenience, the items are sorted by importance and divided into blocks: Mandatory, Important and Desirable. There is also a list of Digital Hygiene Rules and What to Do in an Emergency. How to perform this or that action can be easily found on the Internet, so for the sake of clarity, I present the actions themselves and short explanations. In the final part of the article I will give several real examples.
I tried to put together the most complete collection, but if you have anything to add, write in the comments.
Preventive measures
Mandatory
| Action | Explanation | |
| 1 | Set a PIN code on the SIM card | in case of loss/theft of your smartphone, the swindler will not be able to quickly use your number, you will gain time |
| 2 | Apply at the mobile operator’s office for a ban on actions with a power of attorney | to prevent crooks from making a duplicate SIM card using a fake power of attorney |
| 3 | Issue a ban on registering real estate transactions without personal presence | to exclude the sale of an apartment using a fake power of attorney or fake digital signature |
| 4 | Set up a notification about the issuance of an electronic signature in your personal government services account | if fraudsters issue a fake digital signature in your name, you will know about it immediately |
| 5 | Set up two-factor authentication on government services, tax, mos.ru, and Rosreestr websites | scammers will not be able to log in even if they find out the password |
| 6 | Install caller ID on your smartphone | in most cases, scammers call from numbers marked as fraudulent. But sometimes they replace the number with a real bank number, then see point 40 |
| 7 | Install antivirus on your smartphone | protection against Trojans, stealers and other malware |
| 8 | Keep your smartphone software updated regularly, including security updates | protection against current attack methods and closing vulnerabilities |
| 9 | Create different passwords for different sites and applications or use a password manager | if the password for government services matches the password for a simple forum, then by hacking this forum a hacker will receive a password for government services |
| 10 | Set up an alert for each login to the government services website | if scammers gain access to your account, you will know about it immediately |
| 11 | Set daily spending and transfer limits on a bank card | Fraudsters will not be able to withdraw more than this amount. It will be difficult to increase the limit |
| 12 | Configure receiving confirmations of banking transactions via push rather than via SMS | SMS is an unreliable protocol and is susceptible to eavesdropping and attacks. However, if you are leaving for an area without Internet or in roaming, temporarily return the SMS notification |
| 13 | Apply for a ban on the “Mobile transfer” service at the mobile operator’s office | if the SIM card is compromised, money will not be withdrawn from it |
| 14 | Set your smartphone to hide notification texts on the lock screen | If your phone is stolen, scammers will not be able to read bank codes on the locked screen |
| 15 | Set a code word in the office of your mobile operator | for quickly blocking a SIM card in emergency situations |
Important
| 16 | In your Google (Apple) account, indicate a spare phone number and a spare email | if your account is compromised, this will be needed to restore access |
| 17 | Set your smartphone screen to auto-lock for no more than 30 seconds | if the phone is stolen, it will have time to be locked |
| 18 | Remember the code words and security questions for all the banks you use. | so that in emergency situations, without wasting time, confirm your identity in the call center |
| 19 | Don't choose security questions that are easy to answer, such as your mother's maiden name. | this information is often publicly available or in purchasing databases |
| 20 | Learn by heart the numbers of your loved ones | to call loved ones from a number other than your own in emergency situations |
| 21 | Connect alerts about your credit history inquiries | you will be immediately notified of any intention to issue a loan to you |
| 21.1 | Connect notifications about card transactions | this will allow you to quickly identify fraudulent charges and call the bank without wasting time |
| 22 | Keep the phone number linked to your bank account with you at all times. | If a fraudster issues a duplicate SIM card, you will immediately know about it. Why you can’t keep a separate SIM card for banking transactions |
| 22.1 | For the main card you use to pay in stores and on the Internet, prohibit cash withdrawals and purchases outside your country | Stolen cards are usually used in other countries. If you need to pay for foreign goods/services, create a separate virtual card for this. If you go on a trip, temporarily lift this ban |
| 22.2 | When paying online, do not enter your card details in a pop-up window where the payment system website address is not visible | scammers can create a complete copy of the payment page, but it will lead to a fraudulent server |
| 23 | Disable auto-save passwords on your smartphone and computer | otherwise, if the phone is stolen, the thief will be able to see all the saved passwords, incl. those that were saved from the computer |
| 24 | Set limits on auto-replenishment of SIM card balance | If the SIM card is compromised, scammers will not withdraw all the money from the bank card |
| 25 | Write down the hotline numbers of banks and mobile operators on your main and backup phones | so that in emergency situations you can quickly find and call the hotline |
| 26 | Disable auto-receive MMS on your device | there is an old vulnerability that allows viruses to be downloaded to the device via MMS |
| 27 | Deprive the rights to view SMS and calls from those applications that do not need it | a Trojan can be embedded in a harmless application that has rights to SMS |
| 27.1 | Check the extensions in your browser, remove unused extensions | scammers buy old extensions and upload malicious code as updates |
| 27.2 | Review the applications on your smartphone, remove unused and old ones | scammers buy old applications and upload malicious code as updates |
| 28 | Set up push notifications for emails | so as not to miss an important notification from a government or banking service |
| 29 | Mark as not spam the phone numbers of the mobile operator and banks you use | so as not to miss SMS regarding security |
| 30 | Install antivirus on your home computer | Protects against viruses, Trojans, spyware |
| 31 | Keep your home computer up to date with the latest operating system and application updates, including security updates | this will allow you to close detected vulnerabilities, protect yourself from attacks and the latest versions of viruses |
| 32 | Disable the ability to connect remotely to your computer: disable remote desktop, close external ports | One of the common hacking methods is to try to brute force open ports from potential victims and use simple passwords for Remote Desktop. |
| 33 | Service at the bank through a call center where you cannot change the linked phone number | scammers obtain personal data in different ways and can link their phone to the victim’s account |
| 34 | Set a fingerprint or password for contactless payment with your smartphone (or disable it) | if a cell phone is stolen, the thieves will not be able to pay them |
| 34.1 | On your Wi-Fi router, set a complex administrator password and change the device’s IP address | so that crooks cannot log in as an administrator on a wi-fi router |
| 34.2 | Set a complex password to connect to your Wi-Fi router | to prevent crooks from brute force guessing the password |
Desirable
| 35 | Carry a spare phone with a working SIM card | to quickly block your main phone if it is lost or stolen |
| 36 | Set a PIN code on your smartphone to view files, photos and open instant messengers | if your phone is stolen, your files, contacts and correspondence will not fall to scammers |
| 37 | If possible, prohibit remote access recovery via remote channels | If you forgot your password, create a new account |
| 38 | Apply to the Federal Tax Service for a ban on registering a legal entity using an electronic digital signature | to exclude registration of an individual entrepreneur or LLC in your name using a fake digital signature |
| 39 | Do not use face unlock on your smartphone | If your phone is stolen, the thief can unlock the smartphone using a photo. The likelihood of this happening is low, but it happens, so it's best to protect yourself |
Features of the crime
The basis for this crime is the lies of the attacker and the abuse of human trust for the purpose of material gain. For the legislator, it does not matter how exactly the deception is presented - in real communication between people or in virtual communication.
Article 159 of the Criminal Code of the Russian Federation defines Internet fraud as a crime of moderate gravity, which can be reclassified as a serious violation if the amount of damage is more than 1 million rubles.
The object of the crime is certain property or property rights. One of the main signs of a violation is the voluntary transfer of property or the right to it to an attacker. The article for deception on the Internet also defines the objective side of the crime; it consists in causing property damage by deception. It is important that when carrying out this act there are no qualifying signs of theft.
According to established legislation, the subjective side is determined by direct intent, and the direct subject of the crime is a 16-year-old, sane citizen. Any fraud is based on the criminal’s knowledge of human stereotypes and psychology. Fraudsters are, as a rule, highly erudite people; they know exactly how to influence their victim and what words will be ideal for persuasion. Often high-ranking officials become scammers who, using their official position, influence others.
Rules of digital hygiene
| 40 | If you receive a suspicious or alarming call from anyone, hang up immediately. Don't pick up the phone until you understand the situation yourself. Call back only official numbers | protection against telephone scammers |
| 41 | Do not pay in advance, refuse advance payments in any transactions and situations if the company or person is little known to you | protection against online and offline scammers |
| 41.1 | When making an important and large purchase, carefully check and verify the seller’s documents. Do your due diligence | Fraudsters buy fake passports, punch and forge documents. Then they sell cars and real estate that do not belong to them. In such crimes, the buyer usually loses everything, and the seller takes the property back through the court. |
| 42 | Do not let us photocopy or take a photo of your passport anywhere except in branches of banks and government agencies. Do not send scanned documents by email | We reduce the likelihood of personal data leakage. If they insist on making a copy, carry your own copy with you, in which some of the information is blurred out. If copying cannot be avoided, at least avoid photocopying all the pages. How to issue cards using a scan of a passport |
| 43 | Do not leave a passport with a biometric chip as collateral | anyone who has a biometric foreign passport in their hands can open an individual entrepreneur. At least a green bank has such a service |
| 44 | Before paying online, carefully check the domain | to avoid falling for phishing |
| 45 | Check the transfer details immediately before payment | there are viruses that change the details at the last moment |
| 46 | Do not keep large sums on the card you use to pay in stores and on the Internet. | in the worst case, fraudsters will only be able to steal a small amount |
| 47 | Cover the terminal with your palm when entering your PIN code | card data theft protection |
| 48 | Do not illuminate CVV2 (do not turn the card over again) | card data theft protection |
| 49 | Carefully give permissions to applications for SMS and receiving calls | protection against spyware that steals data |
| 50 | Do not give access to your address book to instant messengers and banking applications | this way you will tell the outside world less information about yourself |
| 51 | Check device administrators in your smartphone settings | there should only be verified applications that really need these rights |
| 52 | Set a password to boot the device if your smartphone model has one | additional protection factor |
| 53 | Apply for an eSim if your smartphone model and telecom operator allow it | eSim is more convenient and reliable than a regular SIM card |
| 54 | Take your time to click on links that require you to enter personal data. If you did, check that the site is real. | One of the main threats that continues to operate to this day is phishing resources. Fraudsters can steal personal data, find out answers to security questions, or plant a virus on you |
| 55 | Do not enter your card details in unknown online stores or applications | they can be hacked and the data of all bank cards stolen. Fraudsters also create legitimate online stores. When purchasing from such a store, your card details will fall into the hands of fraudsters |
| 56 | Be careful on sites with pirated content | You may encounter malware, such as spyware, that steals passwords |
| 57 | Do not run cracked programs or key generators on your computer. If you need to use cracked software, run it on a virtual machine | viruses are embedded in pirated programs and key generators |
| 58 | Do not install potentially dangerous applications: unofficial music downloader, pirated content, etc. | they may contain Trojans |
| 59 | When opening any file that was sent to you, even by people you know, be careful. The most common way to infect a computer is for the victim to launch a malicious file. | The malware can be contained in a file of any format and can be encrypted to bypass antivirus programs. Your friends may not know that the file they send contains malware |
| 60 | Files that you received by email, via instant messengers, or downloaded yourself from the Internet, check on virustotal.com | A phishing email is no different from a regular email; it is one of the main malware infection schemes. Better play it safe. For convenience, install the extension |
| 61 | Abroad, withdraw money from the card only at bank branches | scammers steal bank card data through skimmers and shimmers installed in ATMs in places where there are few people |
| 62 | When abroad, try to pay in cash or contactless by phone | It is advisable not to pay by card. In many countries, criminal networks have been developed to steal card data, through photography, through infected POS terminals |
| 63 | Do not give your bank card to anyone. All transactions must take place in your presence | card data theft protection |
| 64 | Do not log into your accounts from other people's devices | these devices may contain a Trojan or any other malware |
| 65 | Do not store very important files on your computer | If you have to format your computer because of a ransomware virus, the data will be impossible to get back. Better to store on removable media |
| 66 | Do not store important or secret files or correspondence on your smartphone. Be mentally prepared that the phone may fall into the wrong hands | to prevent leakage of personal data and personal correspondence. Make it so that your phone can be given to anyone without any risks |
| 67 | Don't connect to free Wi-Fi | prevent attacks on you through unsecured networks |
| 68 | Install applications only from Google Play/App Store and with a good rating | protection against viruses and Trojans |
| 69 | If possible, avoid using lonely ATMs in places where there are few people | skimming protection. It is best to use ATMs in bank branches or large buildings. There they won't let swindlers commit fraud with an ATM. |
| 70 | Keep large sums in a bank that does not have a remote control connected to it | eliminate the possibility of remote theft |
| 71 | Do not store scanned documents in cloud providers | reduce the likelihood of their leakage, for example when a phone is stolen |
| 72 | Do not root your smartphone | if a Trojan gets in, it will be able to do whatever it wants on your device |
| 73 | Practice locking your device from a loved one's phone | training in case your device is stolen |
| 74 | Do not give your phone to strangers | protection against data theft and installation of malware |
| 75 | Use trusted major telecom operators | In some virtual telecom operators, you can obtain personal data using social engineering |
| 76 | Make VK and FB accounts invisible to anyone except friends | publicly available photos are downloaded from social networks and stored on fraudulent servers used by scammers. It is impossible to delete your photos from such servers |
| 77 | In social network profiles, provide a minimum of information about yourself, take a full-length photo on your avatar, delete it (or delete it), replace your last name with a nickname | Fraudsters use search by photo, phone number, last name and first name. This way they collect information and think through attack options. |
| 78 | Have cash at home | in case you have to block cards and accounts, protecting them from fraudsters |
| 79 | Change periodically: code words, answers to security questions, passwords for personal accounts | personal data can leak even from banks, fraudsters can work in bank call centers, so a good practice would be to periodically change sensitive information, for example |
| 80 | Periodically check the information on the websites of State Services and the Tax Service: digital signatures issued to you, participation in organizations, information about your property, Rosreestr notifications, FSSP. In your mail settings, check that there are no redirects to left mailboxes, as well as suspicious sessions and linked devices | In case of notifications about actions that you did not perform, you need to take action quickly. You can check whether a legal entity is registered in your name at the tax office or here |
| 81 | Change your civil passport periodically | If you treat your passport as a key to all your data and a password to identify your identity, then a preventative replacement of your passport every few years will definitely not cause any harm. And it might even be useful. However, I recognize this point as optional. |
Safety rules on dating sites
As strange as it may sound, you need to be careful when looking for love on dating sites. To do this, just follow a number of simple rules:
- When looking through the profiles of potential husbands/wives, you don’t need to lose your head when you see a beautiful photo and an equally decent resume. Vigilance must always be present.
- You should check the candidate you like by entering his first and last name, as well as a photo, using any search engine on the Internet. Information about the person in the photo will appear in the search results. As practice shows, scammers use other people's photos to attract attention.
- Many men are persistent with ladies in their demand to send intimate photos. You should absolutely not do this, otherwise it will become a reason for blackmail.
- Do not send money to a person you do not know personally, and certainly do not give him personal information that could facilitate hacking of bank data and theft of funds.
- Show indifference to photos and information about sick children or adults where fundraising is required. In this way, scammers often use cover to defraud money.
What to do in an emergency
If your phone is stolen
| 82 | From your spare phone, log into your Google/Apple account and mark the phone as stolen. Or erase device | if there is no spare phone, then do this from the phone of a loved one/friend who is nearby. If you are alone, skip straight to the next point. |
| 83 | Block your SIM card using your mobile operator's hotline | ask a passerby, taxi driver, security guard, police officer to give you a phone number. If there are no people, get to the nearest phone shop |
| 84 | Call the hotlines of the banks you serve, block all bank cards and accounts | act quickly |
| 85 | Block all important accounts (email, government services, tax, online banking, social networks, electronic document management) | |
| 86 | Tell your family and friends that your phone was stolen, and also make a post on social networks | so that scammers do not call friends on your behalf and do not engage in blackmail. Memorized numbers of loved ones will come in handy here. |
| 87 | Write a statement to the police | maybe they will do illegal things from the number, you will have proof that you have nothing to do with them |
| 88 | Log out of all instant messengers on the stolen device | so that the thief does not get the correspondence |
| 89 | Untie a stolen device from your Google account, instant messengers, government services, financial applications, social networks | so that the thief cannot do his business in your accounts |
| 90 | Change passwords for important accounts: email, government services, tax, bank accounts, social networks | to do when a duplicate SIM card has already been issued |
If you receive an SMS about debits that you did not make
| 91 | Make sure that the SMS came from a real bank number or payment system, check that the card balance has actually decreased | it means your card is being used by an attacker, act quickly |
| 92 | Block all bank cards | hurry before the scammers take out all the money |
| 93 | Call the bank, report debits that you did not make | act quickly, take screenshots of the chat with the bank, record conversations with the bank on a voice recorder |
| 94 | Do not rush to write a statement to the police under the dictation of the bank | if money was stolen without your knowledge, it was stolen from the bank, this is very important ! Do not contact the police as a victim. The bank will conduct the dialogue in such a way that the money was stolen from you. But that's not true. Send a claim to the bank stating that the bank is the injured party, not you, you are a witness. The bank is obliged to return the money to your card |
If you were illegally issued a microloan
| 95 | Write a statement about fraudulent activities to the organization that issued the microloan | a large amount of money does not reach the swindlers, but ends up in banks, which means it can be returned |
| 96 | Write a complaint to the Internet reception desk of the Bank of Russia | the injured party is the name of the financial organization that issued the microloan to the scammers |
| 96.1 | Write a complaint to the creditor | demand cancellation of the debt |
| 97 | Receive from the lender copies of the fake loan agreement and a copy of the passport on which it was issued | |
| 98 | Write a statement to the police, attach copies of documents about the fake loan | A very important point is how you define yourself in this statement. Formulate the statement so that the injured party is not you, but the financial organization that did not exercise due diligence and fell for the scammers’ trick. After all, the microloan was issued without your knowledge |
If a fake digital signature was issued for you
| 99 | Call the CA and cancel the certificate | the certificate must be revoked by the certification authority that issued it |
| 100 | Block digital signature on public services | It is worth understanding that blocking in the personal account of government services does not invalidate the certificate |
| 101 | Write a statement to the police |
If an individual entrepreneur has been illegally opened for you
| 102 | File a police report as soon as possible | |
| 103 | Write an objection to the Federal Tax Service about the illegal registration of an individual entrepreneur as soon as possible | |
| 104 | Contact a lawyer if you have taken out a loan for an individual entrepreneur. | |
If you lost your passport
| 105 | Write a statement to the police, get a notification ticket | |
| 106 | Check that you did not have time to register an individual entrepreneur using your lost passport | |
| 107 | Check that you have not become the head of a left-wing LLC | |
| 108 | Check that you have not been issued a loan | |
If the SIM card suddenly turns off
| 109 | Call your mobile operator and find out the reasons for the disconnection | |
| 110 | If a third party has disabled the card, these are scammers. Block bank cards and accounts until the situation is resolved | |
If there was an unauthorized login to your mail account
| 111 | Restore access to your account and change your password | |
| 112 | Block all important accounts (government services, tax, Rosreestr, finance, social networks, electronic document management) | |
| 113 | Change passwords on all important accounts | |
| 114 | Delete a suspicious session, unlink suspicious devices | |
| 115 | Open your account settings and make sure that the scammer has not set up email forwarding to your mailbox | |
| 116 | Check all important accounts for actions that you have not performed | no digital signature has been issued, no individual entrepreneur has been registered, no loans have been taken, no participation in illegal LLCs, no applications for government services have been submitted, no documents have been signed in the EDI system |
If your account on government services has been hacked
| 117 | Block all important accounts (tax, Rosreestr, finance, social networks, electronic document management) |
| 118 | Call the government services hotline and report a hack |
Tinder scammer
On February 2, the British documentary “The Tinder Swindler” was released on the Netflix streaming service. By the end of the week, the film topped the platform's chart. By February 6, it had accumulated 45.8 million hours of viewing and was among the top 10 most successful projects in 92 countries.
The film tells the story of Israeli fraudster Shimon Hayut. He posed as Simon Leviev, the son of Israeli businessman Lev Leviev, known as the Diamond King. The tycoon's fortune in 2022 was estimated at one billion dollars. Shimon Hayut met women from different countries on the Tinder dating app. Through deception and manipulation, he managed to get about 10 million dollars (about 765 million rubles) from them. Hayut spent the money he obtained from crime on meeting new women and living a luxurious lifestyle.
In 2022, he was accused of fraud committed in Israel and sentenced to 15 months in prison for fraud. The swindler managed to be released after five months for good behavior. Some of his victims continue to repay bank loans. The man became a business consultant and continued to run Instagram, to which more than 200 thousand people subscribed. Shortly after the release of the Netflix film, Shimon Hayut deleted his page.
The fraudster who defrauded girls out of millions of dollars became a screen star
Examples
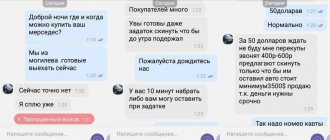
- They stole a phone, gained access to email and the personal account of a mobile operator, changed the code word at the bank, and withdrew money from a credit card. It could have been prevented by following steps: 1, 15, 17, 35, 82-90. Full description in the article.
- The scammers have manufactured a fake cellular base station. The victim made a call from the coverage area of this station, after which the SIM card data fell into the hands of fraudsters. Then they made a clone of the SIM card and, using the Mobile Payments service, stole money from the account. There were no SMS or calls; the victim accidentally noticed that the money in the account had decreased significantly. It could have been prevented by following steps: 13, 24. Full description in the article.
- The scammers hacked the victim's Yandex email and linked his card to the account. Then a small amount was withdrawn in several payments. It could have been prevented by following steps: 91, 92, 93. Full description in the article.
- A classic scheme of telephone scam with the bank security service, the prosecutor and the Central Bank. The scammers were well prepared for the attack, using photos of relatives in their dialogues and intimidating them. As a result, the girl took dictation to apply for loans and transfer money to “protected” accounts. Damage 700k. It could have been prevented by following steps: 6, 12, 40. Full description in the article.
- The victim had a Trojan on her device. A call from the “security service”, a long conversation with the scammers, the woman said that she had received an SMS with a code, but did not mention the code. As a result, the scammers linked their phone number and transferred 230k to their master account. It could have been prevented by following steps: 6, 7, 40. Full description in the article.
- A call from the “security service”, a long conversation, the scammers asked to open the Alfa Bank application and asked if the SMS had arrived. As a result, the victim did not give the code from the SMS, but the money was stolen from the account. Most likely there was a Trojan on the device that sent SMS to the scammers’ server. It could have been prevented by following steps: 6, 12, 40. Full description in the article.
- The crooks somehow learned the code word and the answers to the security questions. Next, they linked their phone number to the victim’s bank account and emptied the card, forcing it into overdraft. It is difficult to put a card without an overdraft into overdraft, but it is possible. Such an attack is prevented by following steps: 33, 79, 91, 92, 93. Full description in the article.
- The crooks somehow found out the victim’s code word and answers to the victim’s security questions, linked their number to his bank account, issued a credit card and withdrew 93,000 rubles from it. It could have been prevented by following steps: 6, 21, 33, 40, 79. Full description in the article.
How to recognize a scammer on a dating site?
In fact, recognizing scammers on a dating site is easy. They have several characteristic features that make them look like scoundrels:
- Showing excessive persistence in order to get to know the victim you “like.” Many women note that they often come across frighteningly persistent men on dating sites who pretend to be decent. Some women do not support communication with such dull gentlemen, but most like it when they are wooed, even after hearing “no”. If you meet such a man on a dating site, you should be wary. You can understand that he is a fraudster by asking him a few bold questions regarding further communication. Many gentlemen-swindlers talk about seriousness in their intentions, despite the fact that they do not know their “chosen one” at all.
- Selection of a potential victim. It does not happen by chance, because not every woman is able to “dissolve” in a virtual romance until she loses her head. Thus, business and successful ladies are unlikely to miss their potential friend from a dating site, since amorous affairs are not a priority in their lives. But quiet, intelligent women, often homebodies, on the contrary, easily fall in love and trust their virtual gentlemen. These are ladies from public sector professions - doctors and nurses, teachers, librarians, as well as housewives, whose lives are not full of colors, but want to plunge into a romantic adventure, like in a whirlpool.
- Rare meetings. Often virtual communication turns into real meetings, and exclusively on the victim’s territory or in an apartment/hotel room rented by the lady after the swindler’s oath promises to reimburse everything. There may be trips to restaurants and other places, which the woman also has to pay for.
How to recognize a swindler on a dating site, says psychologist Natalya Weikselbaumer:
Methods of counteraction
The ways in which a criminal can be exposed and punished include appealing to persons holding positions in law enforcement agencies. In addition, you can find scammers with the help of professional lawyers. Please note that with the second option you can catch the scammer, but not bring him to justice.
In some situations, persons committing fraudulent acts do not fulfill their obligations, while informing the victim that he can contact law enforcement agencies. In this case, the fraudster will be forced to hide from justice, but such games with the Criminal Code will end sooner or later.
The legislation of our country contains several articles containing responsibility for the actions of fraudsters. It is worth noting that the Ministry of Internal Affairs has a department “K”, which fights fraudsters operating via the Internet. The time it takes to file a statement after a crime has been committed is approximately 20 minutes. It happens that the result of the police’s activities is quite impressive.
Due to the development of technology, you can also apply through the global network by sending a letter to the e-mail of a government agency. The application must provide detailed information about the place and time of the crime, as well as other circumstances.