Raiding, or the illegal seizure of someone else's property, as a phenomenon has reached unprecedented proportions in Russia: according to experts, up to 70 thousand raider seizures occur in our country every year. Moreover, now protection from capture is required not only by large corporations, but also by small firms - this is the peculiarity of modern raiding.
If previously a business was seized by typical criminal methods (blackmail, threat, violence, hostage-taking, forgery of documents, etc.), now raiders in the vast majority of cases use apparently legal methods, for example, artificial creation or purchase of an organization’s credit debt - “victims”, amendments to constituent documents and illegal acquisition of shares in the authorized capital, issuance of fictitious debt obligations and bills. For the subsequent legalization of actions to seize a business, a staff of qualified lawyers and attorneys is involved, who use the means of civil proceedings and, as representatives, receive the necessary court decisions. In addition, raiding can be carried out with the “support” of law enforcement agencies - riot police, police, etc.
Unlike civilized business, where mergers and acquisitions of enterprises as forms of reorganization are based on mutual consent and equality of the parties, and the good will of the person transferring the business or part of it is clearly expressed and not subject to doubt, in the case of raiding, the seizure of assets occurs against the will of its previous owners . The founders are deprived of their property and property rights, suffer large losses and lose a source of income, and the raiders, in turn, receive a ready-made business for almost nothing or for an amount several orders of magnitude lower than the market price.
Raiding also has a negative impact on the economic situation, since it eliminates competition, an integral component of a market economy, and leads to the ruin of medium and small businesses and loss of jobs.
What is raiding?
Translated from English, the word “raider” means invader. This borrowing came to the Russian language in its original meaning.
Among the most popular methods of raiders to put pressure on the owners of enterprises they are trying to seize is the threat to open a criminal case against them under a compromising article. At the same time, the attackers promise to release data that will forever destroy the reputation of their victim.
Sometimes threats do not arise out of nowhere. If the owner of the company himself violated the law, for example, withdrew money through shady schemes, then the publication of such data will lead to the loss of clients and a real threat of imprisonment as a result of a criminal investigation.
When preparing a seizure, raiders study the legislation as applied to a specific company and look for its vulnerabilities. Often they initially possess insider information about the actions of the company’s management and violations of the law that have occurred.
Whatever form a raider takeover occurs, it is violent and is carried out without the consent of the owner of the enterprise.
There are three types of raiding:
- White. Simulates compliance with the law. The main actions of the invaders are aimed at disrupting shareholder meetings and conducting additional inspections of the enterprise by regulatory government bodies.
- Gray. A borderline takeover option, when the legal actions of the raiders are complemented by illegal ones, but the violations are not too serious and do not constitute a crime from the point of view of criminal law.
- Black. The most dirty and illegal option for taking over an enterprise. Criminals use blackmail, threats, and forgery of documents, including court decisions. During the procedure for seizing property, it is even possible to force entry into the enterprise itself.
Based on these types of raider takeovers, we can identify typical methods of action of raiders:
- Forceful actions.
- Cascade methods combining different forms of pressure.
- Change of company beneficiaries.
- Pressure on the business owner.
- Appropriation of property contrary to the law with the help of security forces and other government agencies.
- Provoking conflicts among the owners and managers of the company.
All these methods were repeatedly used during raider takeovers of Russian enterprises.
Analytics Publications
In the heart of, perhaps, every businessman, the word “raider” evokes at least an unpleasant feeling of anxiety, and sometimes fear. This is understandable, because quite recently any legal business could become a target for raiders. The concept itself came to us from the English language, where “raid” means raid or robbery. Indeed, the forceful takeover of a business can most accurately be compared to robbery. Today, the issues of protecting a business from a possible attack by “raiders” are still relevant. Lawyers now have quite effective tools and methods to counter raiding in their arsenal. Of course, as in any serious defense, it is impossible to single out just one most effective method; only all of them together can produce results. Business Structuring As the famous saying goes, you shouldn’t put all your eggs in one basket. Many entrepreneurs resort to a business diversification model based on this proverb, thus reducing risks by distributing them between different areas of the company's activities. Less often, company owners think about the fact that the risk of losing a business can also be reduced by dividing it into several business entities in order to provide them with certain functions. For example, one group company may own real estate, another – fixed assets (equipment, transport, etc.), a third – directly conduct the main activities, and a fourth – carry out human resource management functions. Depending on the type of business, this list may be changed and supplemented. Companies that own the most valuable assets become more closed and inaccessible to external intrusion. They are created in the form of an LLC or CJSC, sometimes the property (rights) is transferred to an individual - an individual entrepreneur, usually affiliated with the ultimate beneficiary of the business. Between companies, lease agreements are concluded, as well as agreements for the provision of certain services, on the basis of which they act as one well-coordinated mechanism. Thus, the takeover of one of the firms will not lead to the loss of the business as a whole. In addition, the contracts mentioned above can be terminated, which reduces the value of owning one of the subsidiaries of the target company to zero. This strategy also allows many to optimize tax costs. By dividing a business into several companies, its owner can count on reducing the tax burden through the use of different taxation systems. In addition, internal transactions of a group of companies can be expensed, which in certain cases also has a positive effect on the amount of taxes paid. Protection of shares (stakes in the authorized capital) One of the methods of a hostile takeover is the illegal acquisition of shares or shares in the authorized capital of the company. If the target company operates as a joint stock company, then the most obvious means of combating this type of attack seems to be tightening control over the shareholder register. Depending on the size and nature of the business itself, as well as the type of threat, this control can also be carried out in more than one way.
Large companies, as well as companies planning to receive investments from outside, will most likely prefer to transfer the register of shareholders to a large registrar that values its reputation, and work with which is as formalized as possible.
Smaller companies will seek to concentrate control over the register in their own hands, maintaining it independently.
However, neither one nor the other can be a panacea for a possible stock takeover. In the first case, the registrar may be presented with forged documents, and if the register is maintained directly by the company, the employee responsible for the correctness of the procedures involved may be subject to some kind of illegal influence in order to transfer shares to the raider.
In such situations, encumbering shares with obligations in favor of third parties can be a good remedy. The simplest solution is to pledge shares under a loan obligation.
This method is also applicable to shares in the authorized capital of a limited liability company. After relatively recent changes to the law, it has become possible to register pledges of shares in the Unified State Register of Legal Entities. If there is such a record, it will be impossible to make changes to the Unified State Register of Legal Entities regarding information about the company’s shares.
The pledge can secure the obligations of both the shareholders (participants) of the company and the company itself. The most important issue is the proper registration of all obligations and encumbrances.
Asset protection
Most often, the target of raiders is not the company as such, but the property that belongs to it. In this regard, it is necessary to protect the company's property as a priority measure.
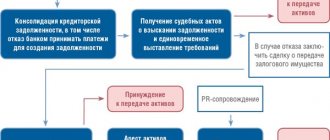
An effective mechanism is the creation of conditions under which property cannot be alienated. Here, as in the case of protecting shares, encumbrance of property with the rights of third parties is applicable. A pledge or mortgage, against which additional financing can be obtained, also provides the owner with a chance to secure his assets.
However, we must not forget about the risks associated with collateral. Debt, for example, to a bank, secured by collateral, is not always controlled by the debtor. If a company has problems with liquidity, arrears may arise, which the “raiders” will not hesitate to take advantage of. By purchasing the debt from the bank, they will be able to take possession of the property on completely legal grounds, and at a price significantly lower than the market. In addition, the acquisition of a default liability from a bank can lead to the raider initiating bankruptcy proceedings, often accompanied by the removal of management and withdrawal of assets. In this regard, in order to protect the business, it is recommended to encumber assets with collateral in favor of controlled persons and organizations.
In addition to the “immobilization” of assets, the above-mentioned company structuring scheme is used.
In addition, such a method of protecting property as business internationalization has proven itself well in this area. Of course, after the speeches of top government officials about the semi-criminal nature of offshore schemes, many will think twice before transferring property to foreign companies. However, the saying “if you put it further away, you take it closer” is still very close to our mental makeup. When the company that owns the main assets is registered abroad and is subject to foreign law, the raider will have to make completely different efforts to seize it than when all the information and documents at the tax office are within five minutes' reach.
Normal operation protection
After the rapid flourishing of the raider movement in our country and the introduction of legislative restrictions, including in the field of criminal law, hostile takeovers began to be carried out using other methods.
Today, in order to paralyze the activities of the target company, deprive it of the strength and time to resist, and ultimately force it to yield to the invaders, so-called gray raiding or “greenmail” is used.
Greenmail is a derivative of the English greenback and blackmail, the first word meaning dollar bill, and the second meaning blackmail. Thus, when applied to the field of mergers and acquisitions, this term means corporate blackmail for the purpose of obtaining money. Gray raiding as such is not aimed at taking over a business. First of all, it pursues the goal of making money on the undervaluation of the company.
In a certain situation, a greenmailer can buy a small block of shares in the “victim” for relatively modest money (to prevent this, it is possible to introduce a statutory ban on the sale of shares and shares to third parties in LLCs and CJSCs). Moreover, the equivalent of these shares in the company’s property can be several times higher than the cost of acquiring the securities.
Then the blackmailer resorts to legal, but exhausting measures for the company of which he has become a shareholder, aimed at complicating the current activities of the company. In particular, endless lawsuits can be filed to challenge decisions of corporate management bodies, demands can be made to convene general meetings of shareholders, a board of directors, conduct audits, revisions, organize staff strikes, etc. It should be noted that legally justified actions of a gray raider should not be subject to legal protection due to abuse of law. The chicane, as such abuse is otherwise called, is prohibited by law, and in the event of litigation, among other arguments, it is necessary to use a reference to this restriction.
In addition to diverting resources to support communication with such a shareholder, the company incurs reputational costs that can affect capitalization and investment attractiveness.
Ultimately, the blackmailer may receive the required compensation for stopping his actions in the form of payment for his shareholding. The price of these shares will be significantly higher than what the greenmailer paid for them. Moreover, it will seriously exceed the market value. In the USA, where greenmail was born and developed into an independent branch of the financial business, such compensation is called a “farewell kiss,” obviously with a very bitter aftertaste.
All the above-mentioned methods of protecting a business are applicable in this case. The selection of an asset custodian company that has the most closed structure can prevent the blackmailer from carrying out his plans. As well as the internationalization of the main companies of the group.
At the same time, it is necessary to understand that the main tool of a greenmail adherent is the use of legal illiteracy of the management bodies of the target company. Incorrect execution of transactions, corporate decisions, failure to comply with the procedure for convening and holding meetings of the company’s management bodies leads to the possibility of appealing them in court.
In this case, the most reliable means is scrupulous adherence to the law in every action of the company's management. In the event of a threat of a hostile takeover, the company must increase its vigilance when drawing up every document, even the most insignificant, not to mention powers of attorney, sales documents, cash documents, and contracts.
In addition, both greenmailers and raiders use all available methods of putting pressure on businesses, including through regulatory and licensing authorities. The risk associated with an unexpected inspection of a particular service dictates the need to legalize all business processes, from commercial activities to labor relations with employees. Total adherence to the law is vitally important in light of the fact that law enforcement agencies can also become an instrument in the hands of a raider (often unwittingly).
As for labor relations, it should be noted that a very effective mechanism for preventing a raider takeover (or neutralizing its results) is to provide management with guarantees in the event of early termination of authority. When changing shareholders, they will first of all change the director, his deputies and the board of directors. Contracts with these persons may provide for the payment of compensation in case of early termination. Sometimes the size of such a “golden parachute” can exceed the benefit of taking over the company or even affect the number of shares that the buyer will retain after the termination of the director’s contract (if the golden parachute includes the exercise of a particular option).
The best defense is offense
This formula is applicable in any struggle, including the struggle for survival in business, but is subject to slight adjustments. An attack is possible and reasonable only with a reliably protected rear, as discussed above. Knowing your enemy is already half the victory.
The victim's knowledge of who is the subject of the attack will help to understand possible ways of developing the situation and plan further response actions.
Depending on the depth of the problem and the current situation, the besieged company must choose certain tools of both passive and active defense.
Passive methods of protection are described above. Active, offensive actions include “mirror” measures against the invader. You can organize endless inspections of government bodies and services, and initiate litigation. As a rule, the raider expects a quick payback for the “project”. Therefore, it is extremely unprofitable for him to delay the process, as well as a situation in which he himself finds himself under attack.
Criminalization (prosecution by law) of raiding in all forms raises concerns among invaders. Therefore, statements to the police, the prosecutor's office, the Investigative Committee, and sometimes the FSB can become effective means of defense against capture.
Raiding in Russia
Unfortunately, the stories of such appropriation of other people's property are not pages of the past of our country. Raiding is the reality of today. More than 70,000 raider attacks take place in Russia every year. Small and medium-sized companies become their victims.
The specifics of the raiders' actions have partly changed. Violent methods of seizure, in which criminal structures played a leading role, have been replaced by techniques that outwardly imitate legal actions: creating accounts payable from the victim company, changing constituent documents and illegally acquiring shares in the company's capital.
Having created problems in the company's work using such methods, raiders attract lawyers and law enforcement agencies, which leads to large losses for the company. As a result, they buy this business for next to nothing.
The global consequences of raiding for the country are expressed in the destruction of small and medium-sized businesses, job cuts and reduced competition in the market.
Famous "victims" of raiders
If we take into account expert assessments, we can conclude: a large number of raider attacks take place in the Russian Federation every year. It should be noted that recently, attackers have begun to direct their attention not only to large, but also to medium and small businesses. The most famous victims of raider takeovers are the following, East Line, Eldorado, Tyazheks, etc. Every year, raider takeovers in Moscow are carried out more and more often. This trend is an extremely negative indicator for the market of modern Russia.
Raider takeover: qualification under Article 159 of the Criminal Code of the Russian Federation
Russian legislation does not contain a specific rule of law within which raiding is punishable. Therefore, in practice, the perpetrators can be prosecuted for specific illegal actions that they commit in the process of seizing someone else’s property. For this purpose, the Criminal Code of the Russian Federation has 10 articles.
When a company is captured through deception or abuse of trust, the actions of the raiders will be qualified as fraud under Article 159 of the Criminal Code of the Russian Federation.
In addition to this article, they may be charged with:
- Article 179 of the Criminal Code of the Russian Federation in case of forcible coercion of the owner of an enterprise to enter into a transaction to transfer property to raiders.
- Article 170 of the Criminal Code of the Russian Federation in case of distortion of information in the Unified State Register of Legal Entities and the state cadastre.
- Article 173 of the Criminal Code of the Russian Federation (parts 1 and 2) when using dummies and shell companies.
- Article 183 of the Criminal Code of the Russian Federation for obtaining secret data that is a trade secret.
- Article 185.5 of the Criminal Code of the Russian Federation for substituting a decision of the company’s board of directors.
- Article 186 of the Criminal Code of the Russian Federation in the manufacture and sale of counterfeit securities.
- Articles 196 and 197 when conducting fictitious bankruptcy.
- Article 303 of the Criminal Code of the Russian Federation for falsification of evidence in court.
- Article 327 of the Criminal Code of the Russian Federation for forgery of other documents not regulated by the articles listed above.
- Article 299 of the Criminal Code of the Russian Federation for illegally initiating a criminal case with the aim of putting pressure on an entrepreneur.
These are not all the rules of law that can be applied to punish raiders. Different company takeover schemes may contain completely different circumstances that will affect the qualification of offenses.
But practice shows that the most common article under which raiders are convicted is Article 159 of the Criminal Code of the Russian Federation on fraud. Depending on the presence of conspiracy, the group nature of the crime, the use of official powers and other circumstances, one of the 7 parts of this article of the Criminal Code of the Russian Federation is applied.
The maximum penalty in this case is imprisonment for 10 years.
Measures to protect the enterprise
Raiders simultaneously act “from the inside” and “from the outside,” destroying trade secrets and blocking the organization’s activities before taking over. As a result, the vulnerability of the enterprise increases many times over.
You have to resist the attack in several directions at once, without having information about who will strike and at what time.
Given the seriousness of the threat to doing business, the Russian market is becoming less attractive for investment than it could be. Protection against raiders is gaining a very significant position and is becoming a separate (quite profitable) business.
Anti-raid measures begin with taking into account important details by the business owner himself.
– All significant positions in the enterprise must be under the control of competent and trustworthy people.
Raiders establish surveillance:
- For the owners and co-shareholders;
- Directors and their deputies;
- System administrator;
- Lawyer of the company;
- Security company;
- Courier service delivering important documents
This means that it is in these areas that significant efforts need to be made to ensure security. A lawyer, financial director, system administrator and others on whom the preservation of trade secrets depends will help you with this.
Additional safety rules:
- The security service must also enjoy unquestioned trust and be reliable and professional.
- Regular monitoring by management across all spectrums of management.
- Legitimacy, transparency and literacy in dealing with taxes, asset accounting, etc.
- Analysis and elimination of vulnerabilities in the company's work.
- Ensuring the protection of any information about the enterprise.
- Analysis of any changes in the composition of the main shareholders, the interest of third parties in the affairs of the company, the activity of regulatory authorities.
- Concealing the work hours and schedules of employees from unauthorized persons. Especially regarding security and courier delivery.
All this should alert and serve as a signal for the lawyer to collect information about cases of possible fraud, and for security guards to be prepared for any unfriendly actions.
A lawyer must be prepared to prove in court the facts of fraud, forgery of documents, intimidation, blackmail and other illegal actions of raiders.
However, given the scale of the ongoing event to seize property, you need to understand that huge sums are spent on bribes, and no one is immune from sudden changes in the behavior of trusted people or security.
How does a raider takeover occur?
The history of the appropriation of someone else's commercial property is rich in various raiding scenarios, which combine different methods of seizure. Let's look at them in more detail.
Raiding methods
A typical stereotype of raiders is people in masks breaking into a company office. In reality, power grips are now rarely used. Attackers began to use more sophisticated methods:
Have a question for a lawyer? Ask now, call and get a free consultation from leading lawyers in your city. We will answer your questions quickly and try to help with your specific case.
Telephone in Moscow and the Moscow region: +7
Phone in St. Petersburg and Leningrad region: +7
Free hotline throughout Russia: 8 (800) 301-39-20
- Social pressure. The raiders are organizing discontent among residents of areas adjacent to the enterprise. Next, the press and regulatory authorities are involved, which identify violations of environmental legislation and various sanitary standards in the course of the activities of this enterprise. As a result, the company’s risks and losses are growing, and the problem can only be solved by reaching an agreement with the raiders.
- Stock manipulation. The easiest way is to buy shares from small shareholders. As a result, the raider ends up with a fairly significant percentage of shares and can influence the work of the company. This influence is more about disrupting its work through litigation and interfering with the decision-making of the shareholders' board. The goal is to bring the company to an unprofitable state, in which its owner agrees to sell his brainchild in order to return at least part of the lost money.
- Bankruptcy. You can bring a company to a state of bankruptcy by buying up its debt obligations and putting forward inflated demands on them to the owner. If he is unable to fulfill them, he will become a debtor and will have no choice but bankruptcy proceedings. And upon its completion, the raiders will buy the company for a pittance.
Such methods are essentially fraud, but from a legal point of view there is nothing to attract raiders for.
Of course, not everyone follows such a thoughtful and sophisticated path of influencing the victim. There are also forceful takeovers with the support of corrupt law enforcement officials and local authorities.
The takeover of leadership by people in masks is used in relation to small successful companies.
In addition, another criminal method of raider seizure is often used - forgery of documents. This scheme is used very often in Russia. Having entered into an agreement with government officials, the raiders draw up a new package of documents for the captured company. She gets a new manager, a different legal address, etc. The real owner thus loses ownership rights to the company.
Scenarios of raider attacks
The development of capture within one of the described schemes occurs according to two scenarios:
- Sale of assets. The purpose of the takeover, in this case, is the complete destruction of the enterprise in the interests of its competitors. Usually a competitor orders such raiding. Having gained control over the company, the invaders sell its equipment and workshops, or even demolish the production premises.
- Acquisition of an enterprise by a competitor. This is how he expands his business and gets his rival out of the way.
Based on the types of raiding described, its scenarios and schemes, it becomes clear that professional lawyers play a key role in the seizure. They look for weaknesses and loopholes in the company's charter documents. Once found, the property is transferred to the name of another owner. Outwardly, everything looks legal and it can be extremely difficult to challenge the alienation of property.
In preparation for a takeover, raiders will learn all possible information about the company's activities and its value. Particular attention is paid to searching for connections of its owners with representatives of authorities and law enforcement agencies.
Raiders do not hesitate to bribe the officials they need.
Reasons and goals of aggressive actions
Raiders usually do not “work” on their own. Their activities are initiated by people who engage in such crimes. There are many raiding companies that carry out orders from competitors to eliminate their opponents, like killers. Only instead of murder, a firm or company is captured. To some extent, raiders are a kind of financial pirates of our time, with enormous capabilities, connections and extraordinary abilities to circumvent the requirements of the law. It is often almost impossible to prove that a company has been raided.
In order to achieve their goal, raiders use the real signatures of the company's owners on the sale or donation agreement. Thus, the takeover of a business is disguised as legal transactions on terms favorable to the attacker.
The following look attractive to raiders:
- Companies with serious assets, shares, land and real estate;
- Real estate and construction companies;
- Intracity chains of stores, stalls;
- Financial firms;
- Computer services;
- Consulting firms, etc.
The most common target is the property itself, the resale of which brings large profits. The assets of the enterprise are subject to sale in order to deprive the previous owner of any opportunity to fight for it. Thus, after the seizure, the raiders actually “tear apart” the company and what remains of it: all buildings, equipment, vehicles, and resell them to different persons. It is unrealistic to collect traces of all the missing property, as well as to force the raider to compensate for the damage caused. At the time of the trial, the invaders have no real estate or money left that could be recovered under the law.
A raider takeover can only be revealed without delay in the first 2 days, until the real estate and other properties are sold to third parties.
The goal may also lie in the consolidation of private business. Raiders often act on the orders of a competitor of the owner of the enterprise, who is interested in absorbing a strong player in the market.
For example, in Yaroslavl there are two networks of farm goods. The owner of one of them decides to increase his own influence, fortune and take the entire market for himself. In fact, to become the only farming network in Yaroslavl. And for this he finds his competitor’s raider. As a result, he either destroys his opponent, or both destroys and seizes someone else’s production.
How to resist a raider takeover?
The legislation of the Russian Federation is constantly being optimized taking into account the threat of raiders. But they find new loopholes, and it’s not for nothing that the takeovers are based on the work of legal experts.
Therefore, businessmen need to be on alert, paying special attention to the following methods of protection against raider attacks:
- Creation of a legal department in the company that will monitor the company’s documents in order to suppress any attempts to take over. To do this, they will have to find loopholes that raiders can exploit and eliminate them.
- Document storage. It is important to ensure their protection from access by third parties and to have notarized duplicates of all statutory documents and other important papers.
- Verified footage. Accountants, lawyers and the head of security must be well-vetted people. This will minimize the risk of them bribing and working for raiders.
Every successful company must consider and implement these anti-takeover measures. If the seizure has already begun, it is extremely difficult to counteract it and, most often, unsuccessfully.
How to protect yourself from a raider takeover of an apartment?
In addition to the seizure of commercial structures, domestic raiding is common. In this case, the scammers target apartments and houses. They assign them using the following methods:
- Illegal court decisions. If the seller of an apartment leaves the country, a third party challenges his right to real estate through the court and the purchase and sale transaction he has completed.
- Deception of lonely elderly apartment owners. This is a common scam in which criminals obtain signatures of gullible single people on title documents for their homes. The apartment is subsequently sold.
- Appropriation of an empty home. Criminals may even covet an apartment whose owner goes on business trips for a long time. In his absence, they draw up fake documents to obtain ownership of the apartment.
To protect against such schemes you should:
- Be attentive to contracts with tenants. Don't trust only verbal agreements. All contracts must be executed by a notary.
- When leaving on long business trips, you need to set the apartment to an alarm system, and store title documents outside it, in a safe place.
Don’t forget about the fraudulent scheme that cohabitants perpetrate. So, after his wife sells her apartment, her common-law husband files a lawsuit demanding that part of the amount be returned to him, allegedly for expensive repairs.
Where to contact?
You can seek protection from raiders in court and law enforcement agencies. To do this, it is important to have evidence of the raider committing actions that can be qualified as:
- Fraud (under Article 159 of the Criminal Code of the Russian Federation).
- Arbitrariness (Article 330 of the Criminal Code of the Russian Federation).
- Extortion (Article 163 of the Criminal Code of the Russian Federation).
Having collected documentary evidence of these crimes, you need to submit a statement to the police and prosecutor's office. If a criminal case is refused, it must be appealed to higher authorities, as well as a lawsuit against the raiders must be filed in court. Only coordinated, legally competent actions give a chance to counter a raider attack.
Enterprise vulnerability factors
As with any form of conflict of interests between a decent person and a criminal, power is most often on the side of the latter. This is explained by both subjective and objective factors. In addition, raiders, as a rule, are fearless and are not afraid of losing everything, because... they transfer all property in advance into cash (cash) or transfer it to trustees. In addition, it is the raiders who are the most inconspicuous figures in the criminal world, which means that going on the run and completely covering their tracks is as easy as shelling pears for them.
There are significantly more methods for taking over an enterprise, company or other form of business than methods for protecting against raiders.
A decent person is obviously in a much more vulnerable position than a criminal. Invaders have a wider range of methods of influencing the victim than the victim has of methods of defense. This happens because the criminal is not limited by moral norms and uses any prohibited techniques and levers to achieve his goal.
- A person who has taken on the responsibility of managing and developing an enterprise is usually absorbed in work and cannot always notice in time the signs of raiders’ interest in his company.
- Conducting business honestly, he counts on the absolute honesty and incorruptibility of persons on whom the preservation of trade secrets and the competent maintenance of accounting and legal documents depend.
- Invaders usually prepare for a raider takeover long before it occurs. At the same time, they sometimes rely on the complicity of government and law enforcement agencies, that is, people called upon to protect the interests of the victim.
- At the same time, for the victim, the attack usually occurs suddenly, without the opportunity to prepare for defense. The owner of the enterprise does not know who exactly he is dealing with, this aggravates his situation.