Two thirds of information leaks do not occur due to malicious intent. In other cases, these are deliberate actions of cybercriminals, employees of the organization or its contractors. Reports about the theft of confidential data increasingly began to appear in the news: for example, in 2022, it was reported that the Elfin APT group switched from destroying data to stealing it using a vulnerability in WinRAR, hackers hacked NASA and stole data about a mission to Mars, The data of the security agency Allied Universal has leaked.
According to a report by Positive Technologies specialists for the second quarter of 2019, targeted attacks prevail over mass ones. More than half of all cybercrimes are committed to steal information. Personal data is the main type of stolen information in attacks on legal entities. Individuals most often risk their accounts and bank card data.
The tactics that cybercriminals use to carry out attacks are described in the ATT&CK matrix, developed by MITER Corporation based on analysis of real APT attacks. There are twelve tactics in total. Each tactic can be correlated with the corresponding stage of the attack:
- Initial access to the system
- Executing code or command (Execution)
- Persistence
- Privilege escalation
- Preventing detection by defense means (Defense evasion)
- Obtaining credentials (Credential access)
- Discovery
- Lateral movement
- Collection
- Command and control
- Data Exfiltration
- Impact
In this article we will look at the techniques that attackers use at the stage of withdrawing (exfiltrating) data from the target system, after they have penetrated the system, established themselves there and collected all the information they are interested in. The principles of detecting attempts to withdraw data and methods for preventing them will also be discussed.
From Jacob to everyone
The term “identity theft” first appeared in print in 1964. In the English-speaking space, this phrase began to be used especially actively in the mid-90s due to the rapid growth of the market for remote services (issuing bank cards, obtaining loans) and the spread of the Internet in the United States.
But identity theft is not a new phenomenon. The first “recorded” case is the biblical legend of Esau and Jacob.
Isaac had two sons. The eldest, Esau, had the right of birthright, and therefore enjoyed special honor before God. At the end of his life, Isaac became blind and was ready to bless Esau's primacy if he treated him to his favorite dish. Then the youngest son and his mother deceive the head of the family: they prepare the food themselves, after which Jacob dresses like Esau and receives the cherished blessing.
Falsifying sources in order to impersonate someone else was practiced even after. From the 3rd to the 7th centuries, messages were published, the authorship of which was falsely attributed to Clement, one of the seventy disciples of Christ, and in the 7th century, a collection of decrees allegedly belonging to the pen of Isidore of Seville, the greatest theologian of that era. Known as the “Donation of Constantine,” the forged will of Emperor Constantine the Great, who in the 4th century proclaimed Christianity the official religion of the Roman Empire, played an important role in the history of Europe and Russia.
Researchers claim that these kinds of fake works and documents were written and circulated to substantiate this or that doctrine within the Christian church.
Already in the 13th century in Europe people could be burned for forging papers - therefore, the phenomenon was widespread. The proceedings in such cases were conducted by the tribunals of the Inquisition.
In modern times in Russia, there were most fake people during the Time of Troubles. After the death of Fyodor Ivanovich, the last ruler of the Rurik family, the royal throne remained vacant. From 1605 to 1608, 17 people pretended to be descendants of Ivan the Terrible, and False Dmitry I and False Dmitry II even occupied the throne. The total term of their reign was about two years. All that was needed for successful deception was knowledge (not necessarily in all details) of the biography of one’s “relatives” and, in some cases, the support of local or foreign elites.
At the dawn of US history, bribed election commissions wrote dead and never-living people onto ballots, and then threw them into voting baskets. Gangsters of the Wild West killed travelers in order to take possession of their clothes, identification papers and impersonate them.
The mafia in the USA eliminated witnesses, stole their documents and made up “their” people. They went to trial and refused to testify. This prompted the authorities to create the Witness Protection Program.
With the advent of credit cards in the late 50s, identity theft became commonplace. The scheme looked like this: scammers called different apartments by phone and told the owners that they had won a big prize. All you had to do was provide all your personal data - credit card numbers, insurance policy, passport and other documents. This allowed thieves to gain access to a person's credit card and take money in their name. After they stopped believing phone scammers, they began to study garbage dumps: that’s where they could find checks with personal information stamped on them. By the end of the 60s, this type of fraud had faded away.
A new wave of identity theft began in the 80s. The US authorities passed a law that obligated employers to check the documents of their employees. This forced illegal migrants to look for fake IDs, certificates, etc. - mostly they used the papers of people who had already died.
In Russia, Herzen, Trotsky, Lenin, Stalin and other revolutionaries lived on false documents, from populists to anarchists, right up to the February Revolution, and after it - opponents of Soviet power and swindlers of all stripes.
In 1937, Vladimir Golubenko, who escaped from the Gulag, stole a passport in the name of Valentin Purgin. Nothing is known about the real owner of the document, but the rogue who pretended to be him managed to get a job at Komsomolskaya Pravda using fake IDs. He quickly moved up the career ladder, and by 1939 he became deputy head of the military department. Then Purgin-Golubenko appropriated the Orders of Lenin and the Red Star to himself, consistently falsifying reports about his own achievements. The apotheosis of history was the forged papers about exploits in the Soviet-Finnish War and receiving the title of Hero of the Soviet Union in April 1940. Three months later he was exposed, and three months later he was shot.
It seems like identity theft is a trick from pre-computer times, but it's not. An interesting case occurred five years ago: 53-year-old American David Gilmour posed as the guitarist of Pink Floyd, not being the least bit like his star namesake, and was treated for free for $100,000. Arriving at the hospital, he stated that the group was currently on tour in the USA and the artists did not have time to arrange insurance. The rascal knew a lot about Pink Floyd and the UK. Touched, the clinic administration agreed to treat him for free, and he did not skimp on autographs and did not refuse the doctors photos together. Gilmore and her staff even created a "tour" schedule to complete the course.
After his departure, they suspected something was wrong: it’s strange that the guitarist of a legendary band that sold a quarter of a billion albums doesn’t have the money to pay for medical services or international insurance, right? Gilmore was ruined by his impudence: four days later he returned to “get treatment” and was arrested.
Identity theft is the basis of the plot of many Hollywood films, such as Wu's Face/Off, Winkler's Network, Blomkamp's Elysium, Serra's The Unknown and Antonioni's Profession: Reporter.
How to steal identity
“Identity theft” refers to any use of someone else’s personal information for profit. The Russian translation does not accurately reflect the essence of the phenomenon: in fact, it is impossible to steal someone’s “personality”. Attackers steal personal data, a copy of unique information about a person: full name, documents, credit card and bank account numbers, profession, salary, place of work, passwords and account logins, area of interest, etc. That is, any information that belongs only to the owner, which he did not want to share.
Identity spoofing is used for various purposes: stealing passwords and credentials, obtaining financial information and material assets, and often just for fun. Illegally obtained information is sold; Having a password, they hack a person’s accounts in other services, etc.
How common is this phenomenon? The largest database of hacked accounts, Have I Been Pwned, contains over 5 billion.
There are no official statistics in the CIS, but in the Gotcha.pw database, which publishes a list of hacked emails from different countries, there are 48 million accounts in the .ru zone, 5.5 million in the .ua zone and more than 1 million in zone .by.
In the United States, according to a study by New Javelin Strategy & Research, last year 16.7 million Americans became victims of identity theft, that is, every twentieth person in the country.
Losses from personal data fraud in the United States for the year amounted to $16.8 billion—that’s how much Yandex and Mail.ru cost together, while VTB Bank is $2 billion “cheaper.”
There are no such statistics for Europe, but according to European Commission surveys, 8% of EU residents said they were victims of fraud with their personal data in 2022. The Poles and Austrians suffered the most - 12% of the population, the Greeks - 3% - the least. In general, such crimes were committed against more than 50% of Internet users in Austria, the Netherlands, Sweden, France and the UK. At the same time, 30% of users in the region know nothing about identity theft.
Leaders of 69% of European companies do not understand how their brand name can be stolen and used and how to protect themselves from such “theft”, and 60% of large corporations have never calculated the risks of cyber attacks, although attackers are increasingly resorting to this type of fraud.
Media outlets may be closed for distributing materials containing personal data.
The Federal Service for Supervision of Communications, Information Technology and Mass Communications may terminate the activities of a mass media outlet if facts of dissemination of materials containing personal data and other systematic violations of the requirements of the law committed by the editors of the publication have been established. This is what the Supreme Court of the Russian Federation decided.
The essence of the dispute
For violation of the requirements of Article 4 of the Law of the Russian Federation of December 27, 1991 N 2124-1 “On the Mass Media” and the publication by the editors of the newspaper “Labinskiye Vesti” of materials that contained personal data of a minor citizen, namely last name, first name, information about school, in which a minor is studying, without her consent and the consent of her legal representative, as well as a number of other articles with personal data of minors, the Office of the Federal Service for Supervision of Communications, Information Technologies and Mass Communications issued a written warning about the inadmissibility of disseminating information through the media that constitutes a secret specially protected by law, to the chief editor of the media of the newspaper “Labinskiye Vesti”. However, the editor-in-chief did not respond to this warning and continued to publish personal data of citizens without their consent. Therefore, the Office of the Federal Service for Supervision in the Sphere of Communications, Information Technologies and Mass Communications filed a claim with the Krasnodar Regional Court to terminate the activities of the Labinskie Vesti newspaper.
The court's decision
By the decision of the court of first instance, the claim of the Office of the Federal Service for Supervision in the Sphere of Communications, Information Technologies and Mass Communications was satisfied and the newspaper’s activities were terminated. As an appellate authority in this process, the Judicial Collegium for Administrative Cases of the Supreme Court of the Russian Federation. In the ruling of the Supreme Court of the Russian Federation dated June 24, 2015 N 18-APG15-7, the judges did not find any grounds for overturning the decision of the trial court. The reason for this decision was the fact that, by virtue of Article 4 of the Law of the Russian Federation of December 27, 1991 N 2124-1 “On the Mass Media,” it is not allowed to use the media to disclose information constituting a state or other secret specially protected by law. The amendment to Article 16 of this law determines that the grounds for termination by the court of the activities of a mass media outlet are repeated violations by the editorial board of the requirements of this law. Such violations must occur for at least twelve months. How this happened in a controversial situation, about which the registration authority issued written warnings to the founder and editor-in-chief. In addition, the judges noted that according to the provisions of Article 3 of the Federal Law of July 27, 2006 N 152-FZ “On Personal Data”, such data is any information that relates directly or indirectly to a specific subject of personal data. This information, in particular, includes last name, first name, patronymic, year, month, date and place of birth, address, family, social, property status, education, profession, income and other information. In accordance with the requirements of the law, the processing of personal data can only be carried out with the written consent of the subject of the personal data. Therefore, the editorial office that has gained access to personal data must ensure the confidentiality of personal data by depersonalizing it. There was no objective evidence that the newspaper’s editors had exceptional circumstances for disseminating personal data in connection with the protection of public interests.
Splitting consciousness
Is it difficult to steal someone else’s “I” and what will be the penalty?
We warn you: all unauthorized operations with personal data are a violation of the law. Art. 272 of the Criminal Code of the Russian Federation provides for imprisonment for up to 2 years for using someone else’s page or personal information. If hacking an account led to serious consequences, for example, the suicide of the owner or his loved ones, created a danger to someone’s life, or caused large monetary damage, the attacker faces up to 7 years in prison. According to Art. 159.6 for the simplest fraud on the Internet you can get up to 2 years of restriction of freedom or a fine of an annual salary, and for a more complex one (committed by an organized group, for an amount of more than 1.5 million rubles, etc.) - up to 10 years in prison.
The names of the characters have been changed.
The first option is to buy another person’s already hacked page. We type “social network account store” into a search engine and get hundreds of links to trading platforms. On Instagram and VKontakte they cost pennies - from 15 rubles apiece.
For the sake of experiment, we buy two accounts: one with more than 1000 friends, and the second one belonging to the editor of a group with 20,000+ subscribers. Each costs 30 rubles.
The first is Peter. He is married, plays American football, and enjoys internet jokes. Administers many small groups, he has 1415 friends. What could a scammer do about this? For example, wait until Peter goes to bed, quickly change the password and organize a mailing to all friends with a request to urgently transfer money to someone else’s account (punishment: up to 4 years in prison and a fine of up to 36 monthly salaries). Or go into his correspondence, look for incriminating evidence there and blackmail Peter (punishment: up to 4 years in prison and a fine of up to 36 monthly salaries for the “lightest” part of the article). Or steal personal photos and use his identity (punishment: up to 2 years in prison and a fine of up to 18 monthly salaries, provided that nothing is done to the page that aggravates the guilt).
The second is Igor. He edits a group that has 50,000 subscribers. Attackers could publish posts on behalf of the community (punishment: up to 2 years in prison and a fine of up to 18 months' salary). Or try to persuade the public administrator to grant similar powers to them - and resell the account, which in this case will cost an order of magnitude more. Or send a newsletter on behalf of the group to different users, invite them to another community, give them phishing links, ask for money (punishment: in both cases - up to 4 years in prison and a fine of up to 36 monthly salaries). Or, again, try to find incriminating evidence in the correspondence and engage in blackmail.
We inform both heroes that their accounts have been hacked, ask them to change their passwords, and conduct a brief educational program on the topic “Internet Safety.”
The second option is to steal other people’s data yourself.
We go to the social network “VKontakte”. In the search for documents, enter “passport jpg”. Lo and behold, we found hundreds of scanned documents from all over the CIS.
We choose one of them - in the name of Lyudmila Vasilevskaya, a 24-year-old girl. We have a passport, which means we know the city in which she lives and her date of birth. We enter her first and last name into the people search and immediately find Lyudmila. There is no information on the page about the place of work and study; such a person is not registered on other social networks.
The passport indicates the place of birth - we are looking for friends in this city. They all studied at the same school - probably in the same place as Lyuda. We look at the page and from the photo we understand that she is a salesperson in a bag store in her hometown. Let's find out the address of her work. The girl has a mother and brother, she loves them very much and lives with her family.
Lyudmila is actively looking for a life partner and loves flowers. She has no pets. Knowing where the girl works and who she works for, we proceed from the fact that she is unlikely to earn more than 15,000 rubles in the store. Her family is not rich: all the photos were taken on an inexpensive smartphone, Lyuda does not have a personal car, and she does not travel abroad. Our “victim” constantly writes about what she did and how she lives.
In an hour we learned quite a lot, and we have a scan of Lyudmila’s passport. How could the “knights of profit” use all this?
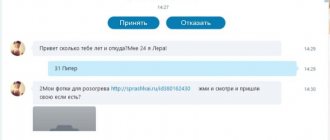
First of all, completely clone the page and create a “duplicate” of it on other social networks. After this, the most active VK friends of Lyuda (who liked her posts throughout the year) from other cities are searched. A swindler can flirt with them, and then try to lure money out of particularly gullible people under various pretexts. For example, say that you don’t have enough for a ticket or a new beautiful dress. These people do not know each other, and they are unlikely to be able to exchange information with each other. Even if the scammers are exposed, just because they communicated with someone not on their own behalf, nothing will happen to them (punishment: if they managed to lure out money, then up to 4 years in prison and a fine of up to 36 salaries; if not - “ modest" 2 years of imprisonment and a fine of up to 12 salaries).
The second option is to search and add all your VK friends indiscriminately on another social network. In this case, the simplest scheme is to send phishing links in order to find out their username and password. An example of such a letter: “Hello, this is Lyuda [phishing link to page]! Now I’m on Facebook, let’s be friends.” But in fact, the user goes to a scam site designed exactly like FB. Suspecting nothing, you enter your username and password on this pseudo-Facebook - that is, you actually tell them to the attackers (punishment: if the data was resold, then up to 4 years in prison and a fine of 36 salaries).
However, you can create a clone of the page here, on VK, and engage in fraud under the guise of dating to find a partner.
The spectrum is wide - from requests to “put it on your phone” to blackmail and fraud with credit cards. And most importantly: knowledge about People will help an attacker create a plausible legend - “copying” a living person is much easier than sculpting a person “out of nothing.”
Or you can create a page for a wealthy guy who is interested in Luda. There is enough information about the victim to manipulate him. After the criminal gains Lyudmila’s trust, he may try to lure money from her - for example, to come to his “passion” (punishment: if the trick is successful, then up to 4 years in prison and a fine of up to 36 salaries, if not - 2 years behind bars and a fine of up to 12 salaries).
The third way is to create accounts in Luda’s name. Use her passport to confirm various pages on social networks or online stores, as well as payment systems, and then either resell them or use them for fraud. The price of a well-promoted, verified VK or Instagram account is from 5,000 rubles, Yandex.Money and WebMoney wallets are from 1,500 rubles. Confirmed accounts will not be blocked, even if you log into them from the TOR or VPN network (punishment: 4 years in prison and a fine of up to 36 salaries or, if you’re lucky, up to 2 years of correctional labor and a fine of up to 12 salaries).
The fourth method is fraud with passport data. Fraudsters can find accomplices on the Internet and register real estate, a car or a SIM card for Lyudmila; register under her name with credit institutions, bookmakers, as well as take out a quick loan or participate in trading on sites related to binary options and Forex (punishment: up to 6 years in prison and a 500 thousand ruble fine if accomplices took advantage of their official position , or up to 2 years of restriction of freedom and a fine of up to 12 salaries). Or simply resell your passport photo on the darknet - for a modest couple of dollars, but as many times as you like (punishment: up to a year of correctional labor and a fine of up to 6 salaries).
The requirement to present a passport at the checkout is not a violation
Violation of the procedure established by law for collecting, storing and using information about citizens is subject to administrative punishment. However, when returning goods to a buyer in a store, the cashier is required to check the passport and fill out financial documentation, in accordance with legal requirements. The Supreme Court of the Russian Federation that such actions are not a violation of the law on the protection of personal data.
The essence of the dispute
By resolution of the prosecutor's office, a case was initiated against the trading organization for an administrative offense under Article 13.11 of the Code of Administrative Offenses of the Russian Federation. This violation was expressed in the fact that in the organization’s store, during an inspection for compliance with the legislation on personal data, it was established that the organization processes personal data of individuals by collecting, systematizing, accumulating, storing, clarifying (updating, changing), extracting, using , transmissions. At the same time, the processing of customers’ personal data carried out by the organization does not fall under the exceptions established in Article 22 of the Federal Law of July 27, 2006 N 152-FZ “On Personal Data”. The inspection was carried out at the request of a citizen who expressed a desire to return the goods to the Pokupochka store. At the same time, he was asked to fill out a mandatory application in which it was necessary to indicate personal data in order to return the funds, if there was a check. By virtue of Article 5 of the Federal Law “On Personal Data”, the demand for personal data is redundant. Based on this, the organization was brought to administrative responsibility by the magistrate for committing an administrative offense provided for in Article 13.11 of the Code of Administrative Offenses of the Russian Federation in the form of a warning. However, the organization did not admit its guilt and appealed the decision of the magistrate.
The court's decision
The higher courts agreed with the conclusions of the magistrate about the presence of this administrative offense in the actions of the company. However, the Supreme Court of the Russian Federation, to which the organization filed a complaint, by resolution of June 15, 2016 N 25-AD15-3, canceled all judicial acts adopted in the case and found the organization not guilty. The judges noted that in accordance with the law on personal data, the processing of personal data must be carried out in compliance with the principles and rules provided for by law. The processing of personal data is carried out with the consent of the subject of personal data to the processing of his personal data. However, according to the provisions of the Law of the Russian Federation of February 7, 1992 N 2300-1 “On the Protection of Consumer Rights,” the buyer has the right to refuse to fulfill the sales contract and demand a refund of the amount of money paid for the goods. Decree of the Government of the Russian Federation of January 19, 1998 N 55 approved the Rules for the sale of certain types of goods, according to which the buyer has the right to return the purchased goods to the seller and receive the amount of money paid for it. At the same time, the seller is obliged to comply with the Regulations on the procedure for conducting cash transactions with banknotes and coins of the Bank of Russia on the territory of the Russian Federation, approved by the Bank of Russia dated October 12, 2011 N 373-P (lost force from June 1, 2014 due to the publication of the Bank’s Directive Russia dated March 11, 2014 N 3210-U). In accordance with which, the procedure for conducting cash transactions for the purpose of organizing cash circulation on the territory of the Russian Federation provides for the issuance of cash by the cashier directly to the recipient specified in the cash order, only upon presentation of a passport or other identification document in accordance with the requirements of the legislation of the Russian Federation . Based on these norms, the situation with the return of money to the buyer from the organization’s cash desk on the basis of his written application indicating his last name, first name, patronymic and identification document details does not contradict the requirements of the law. Requesting the specified personal data is not redundant. Therefore, there are no grounds for bringing the organization to administrative liability.
Rules of digital hygiene
We talked about safety in the modern world of digital technology with Ksenia Ermoshina, a researcher at the Citizen Lab at the University of Toronto, administrator of the telegram channel @parisburns, and ethical hacker d0gberry, administrator of Gotcha.pw.
Ksenia:
— Most leaks come from large companies. Corporations allow them because it benefits them. And unreported so-called zero-day vulnerabilities discovered by hackers could be used by governments to spy on citizens.
Legally, data in large corporations is stored in one place, although they are geographically separated. And this is also, of course, bad.
Will they ever invent a system that cannot be hacked? As soon as someone declares that they have come up with something similar, such a system will immediately cease to be protected and will turn into a sweet bait that attracts hackers from all over the world.
Now everyone is talking about blockchain - I think that solutions based on decentralized systems of this type are possible, but we need to find a way to make them accessible to “mere mortals”, because for now they require large amounts of memory on computers and a lot of electricity.
The approach to data protection should be developed and implemented at three levels: user, infrastructure and legislative.
As for the first of them, we must develop a culture of consuming Internet content and using devices, programs and sites. Explain to people that they are not just “users”, but also active participants in the information market, that their data is valuable in itself; introduce users to specific security tools; instill general behavioral norms.
Data hygiene - rules of conduct related to online and offline security. There are no trifles in this matter: you cannot leave the computer on when you leave home or even briefly leave the room where there are other people, no matter how much you trust them; It is mandatory to install all updates on gadgets. Well, the top is various programs for encrypting communications (PGP, Signal, etc.) and the hard drive (VeraCrypt, for example), as well as the use of operating systems with a high degree of security (such as Tails).
As with health, hygiene depends on the level of risks you are exposed to: for a person working in an office, washing your hands with soap is enough, but if you are a doctor or a chef, you may have to add a protective mask and cap, gloves and disinfectants. solutions. But even at the most basic level, data hygiene is a concern for absolutely everyone.
Many guides have been written on how to protect yourself - for example, Surveillance Self-Defense from the Electronic Frontier Foundation or the RosKomSvoboda Safe project, both in Russian.
At the legal level, responsibility for the collection and storage of our personal information (this does not mean the data that we create ourselves through social networks and applications, but that known to the state, banks, insurance companies, etc.) lies with these organizations. It is necessary to develop a legislative framework that would not leave room for artificial data leaks and manipulations.
And from an infrastructure point of view, it is necessary to improve technical documents regulating the activities of data centers, as well as data transfer standards.
d0gberry:
— Since hacks happen all the time, it can be argued that companies do not particularly care about the security of credentials. Cases of careless handling of personal information are constantly emerging: a month ago, for example, it turned out that T-Mobile stores the passwords of its European customers in plain text. That is, if this database is stolen, it can immediately be used to hack accounts.
On the dark web, personal information can be sold for just a couple of dollars. And large leaks from hacked accounts often occur. Identity theft does not require special skill.
In my database there are 1.5 billion accounts with decrypted passwords, but there are also those that contain many more encrypted passwords, and decrypting them is only a matter of time. New leaks happen all the time, so you just have to accept it and move on with your life.
Use a VPN to protect yourself from hackers
Public Wi-Fi networks do not require authentication. Great, right? Hackers are of the same opinion, because they don’t need it either. They may resort to Man-in-the-Middle techniques or even install a fake Wi-Fi access point to intercept your personal data.
If you need Internet on your laptop, it is better to connect it to a 4G mobile network by turning on tethering mode on your phone.
Better yet, use a virtual private network (VPN) as your personal Internet gateway.
How can a VPN help you prevent hacker attacks?
A VPN redirects traffic, hiding your IP address and preventing scammers from tracking you. It also encrypts the data you send, so even if someone intercepts it, they won't be able to read it. This also applies to your Internet provider. So, VPN is a great way to protect your personal data on the Internet.
This method has a number of other advantages besides online protection. With a VPN, you can visit sites blocked by your provider - in some countries this may be Facebook, Twitter, VKontakte. The ability to bypass local content blocking can be useful when traveling abroad if you need access to your account, which may be closed to “foreign” users.
There are free VPNs, but they may come with certain conditions. It’s better to use the paid version - you shouldn’t skimp on protecting your data.